by admin | Sep 10, 2025 | Data Governance, Security/Breaches
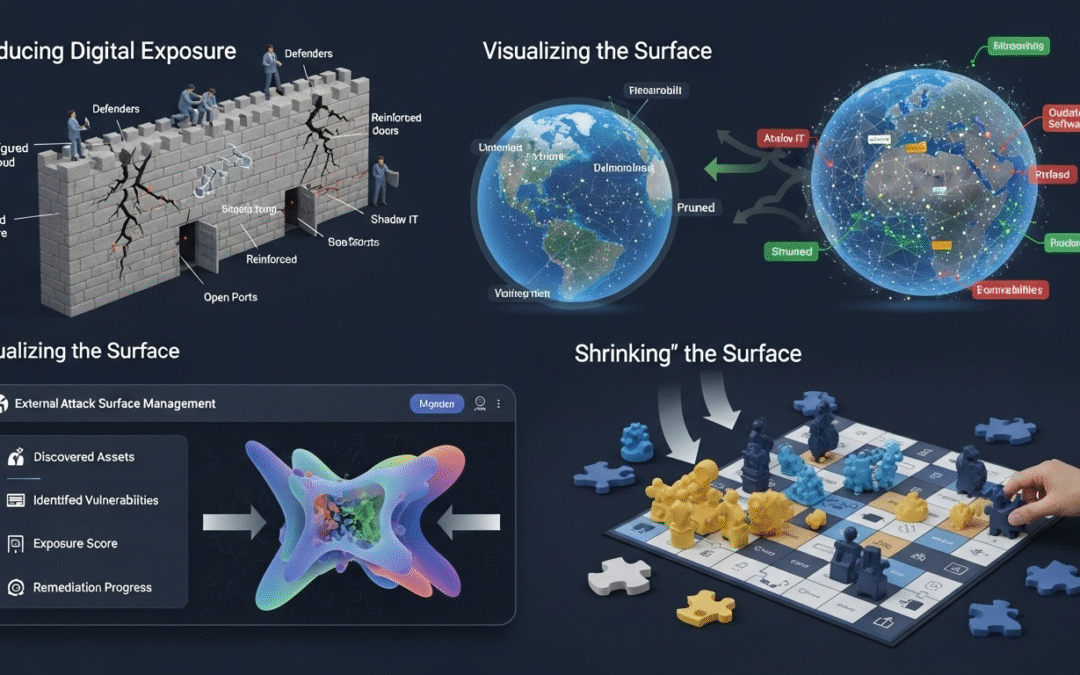
Introduction: From Perimeter Defense to Digital Exposure Management Historically, cybersecurity strategies were built around the concept of perimeter defense. In the late 1990s and early 2000s, organizations relied heavily on firewalls, antivirus software, and...
by admin | Sep 9, 2025 | Security/Breaches
Table of Contents Executive Summary Understanding CVE-2023-42480 SAP’s Response and Patch Release Implications for Data and Security Teams Key Takeaways Conclusion: ERP Security at a Crossroads Source 1. Executive Summary SAP, the global leader in enterprise...

by admin | Sep 9, 2025 | Data Governance, Security/Breaches
In a chilling reminder of open-source vulnerabilities, a fresh wave of malicious npm packages—carefully crafted to impersonate legitimate modules—has been uncovered in an ongoing campaign targeting software developers and cloud environments. The coordinated attack,...

by admin | Sep 9, 2025 | Security/Breaches
A newly observed advanced persistent threat (APT) group, dubbed “NoisyBear,” has launched a sophisticated cyber campaign targeting energy infrastructure operators in Kazakhstan. Leveraging custom malware and living-off-the-land binary (LOLBin) tactics, the...
by admin | Sep 9, 2025 | Data Governance, Security/Breaches
Threat at the Core of Developer Trust In an unsettling reminder of the fragility of software supply chains, security researchers have discovered a series of malicious NPM packages masquerading as legitimate Amazon Web Services (AWS) software development kits. These...

by admin | Sep 9, 2025 | Data Engineering, Security/Breaches
In a chilling development that exemplifies the escalating arms race in cybersecurity, a novel malware campaign—nicknamed “GPUGate”—has been uncovered, deploying advanced evasion techniques by abusing both the Google Ads infrastructure and the computational properties...







